Shadow AI attack paths: OAuth, prompt injection, and a 30-60-90 plan
Lock down Shadow AI with an evidence-based 30-60-90 plan for OAuth, prompt injection, and browsers. RockCyber’s executive playbook.
Shadow AI is a governance gap that has grown into a breach factory. Nearly every enterprise has unsanctioned AI in play. One study found 98% of companies had employees using unauthorized apps, and more than half of employees used high-risk OAuth apps. That is the reality boards are funding and attackers are exploiting. In this piece, I lay out what I am seeing across clients, why identity and data governance are the first fixes, and a concrete 30-60-90 plan any CISO can run this quarter.
The uncomfortable truth: data governance first, security second
Shadow AI thrives in messy inventories, loose approvals, and opaque access. Governance failures give attackers their opening. Security controls clean up the mess after the fact. The data shows it. Shadow AI incidents accounted for a significant share of breaches in 2025 and cost more on average when AI access controls were missing. Users copied and pasted sensitive data into free AI tools at scale. If you cannot answer who is using which AI app, with what data, and under which scopes, you are not running an AI program. You are funding an AI risk pool.
Here is my stance. Allow AI systems tiered by data class with a kill switch, provided that every AI tool is logged in a registry. That means a visible list of approved AI uses, mapped to data classes, with explicit owner, scopes, and a dead-man switch for revocation. This is the CREATE and RUN of CARE in motion, where you create rules and a registry, then run them with monitoring, reviews, and fast containment.
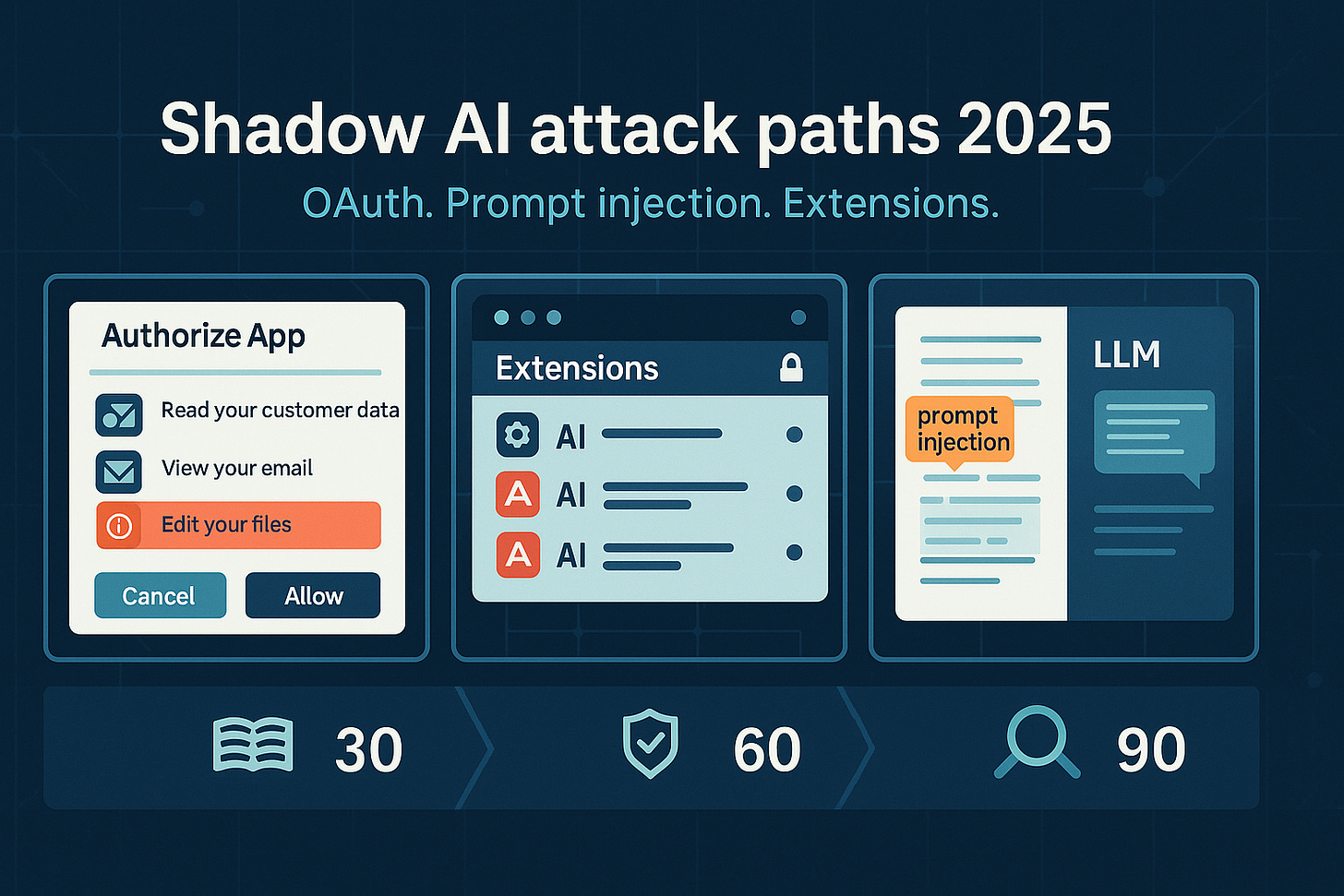
Attack path 1: OAuth abuse through third-party AI integrations
The most painful 2025 incident exposed how one AI integration can turn into hundreds of downstream breaches. Attackers stole OAuth tokens tied to a third-party AI chat integration (Drift) and systematically queried Salesforce data across many tenants. Stolen data included core objects and even sensitive credentials, such as AWS keys and Snowflake tokens. Cross-tenant volume analysis by the SaaS provider later helped bound the blast radius.
What made it hurt particularly bad was scope sprawl. Unvetted apps connected with broad read or write scopes, often outside security review. That is Shadow AI in a nutshell. The framework mapping is boring but useful. This pattern aligns with MITRE Initial Access via trusted relationships and Exfiltration over web services. It also addresses OWASP LLM Top 10 items related to supply chain and insecure plugin design. According to NIST AI RMF and ISO 42001, supplier security and continuous monitoring are governance issues that should have been addressed before security had to intervene.
What to do fast:
Revoke and reauthorize affected tokens. Monitor reuse and anomalous IPs.
Enforce least privilege on third-party scopes and partition access by role.
Stand up SSPM or equivalent reviews to inventory and prune risky OAuth apps.
Attack path 2: prompt injection through connectors and untrusted content
When you connect an LLM to your drive, inbox, or calendar, you have given it hands and eyes. In 2025, researchers demonstrated how a single poisoned document shared with a connected account could be leveraged to flip convenience into exfiltration. The hidden instructions looked like content. The model treated them like commands. Secrets in a drive were pulled into an outbound request without the user ever being aware of it. The researcher’s summary was blunt: zero-click, share a doc, game over.
This is not academic. Any system that allows an AI to read or act on user content is vulnerable. The mitigation pattern is simple to say and hard to do:
Isolate and sanitize inputs so data is not treated as instructions. Use sandboxing and content stripping.
Insert guardrails that require explicit confirmation for risky actions or bulk searches.
Label high-risk data sources as 'NO_AI' and enforce this designation in gateways and DLP.
Detection is fragile, but you can scan for telltale artifacts, such as tiny white text in documents, and watch for AI behaviors that do not match the user’s request. Log prompts and outputs to investigate anomalies. No logs, no trust. No trust, no AI.
Attack path 3: malicious AI browser extensions and plugins
The fastest-growing Shadow AI surface is in the browser. Employees install AI helpers that promise productivity. Attackers notice. In early 2025, dozens of legitimate extensions were hijacked to deliver information-stealing malware to millions of users. Titles sounded familiar. Updates arrived automatically. Data quietly walked out the door.
Researchers have also demonstrated that even low-permission extensions can inject prompts into AI tools and exfiltrate sensitive data. That is a “man in the prompt” that rides normal browsing sessions. The kill chain is straight out of the web attacker’s playbook: social installs, auto-updates, user context execution, cookie and token theft, exfiltration over normal web traffic, and persistence until someone notices.
What works here:
Managed browsers and extension allowlists. Inventory what is installed. Remove the rest.
Block known-bad AI extensions at the policy layer.
Treat extensions as code running with the user’s keys. If you would not ship it to prod, do not allow it in the browser.
What I saw on the ground: a vendor LLM integration pulled secrets from a shared drive
A real client story. Names withheld to protect the innocent. A team connected a vendor LLM to a shared drive to “speed research.” No registry entry. No scopes review. A week later, our logs flagged unusual outbound traffic that appeared to be harmless image fetches. Under the hood, the queries embedded API keys that were stored in a hidden folder from a prior project. The vendor’s connector was doing what it was told by content that it should have treated as data. We contained it, forced reauthorization with the least privilege, and applied a 'NO_AI' label to the drive. That was the easy part. The hard part was explaining to leadership that nothing “malicious” happened in the classic sense. Their process did exactly what it was configured to do. That is Shadow AI.
Governance over gadgetry: why “LLM gateways fix everything” is wrong
I like LLM gateways. Clients use them. They don’t fix identity, OAuth governance, or agent permissions. If your marketplace is full of high-scope apps nobody owns, a gateway won’t save you. If your users pipe untrusted documents into connected assistants, a gateway masks symptoms. If you run autonomous agents with shared creds and no logs, a gateway cannot explain who did what. The 2025 data tells the same story in that nearly all organizations with AI-related breaches lacked proper AI access controls. Many also had no AI governance policy.
CARE in practice: create the rules and run the program
Two moves change the game within 30 days. First, CREATE: approve an AI use policy, define data classes, and publish an AI registry that every tool must live in. Second, RUN: monitor OAuth scopes, review consents weekly, and revoke anything outside the registry. This is not compliance theater. It is how you stop scope creep and see where your data flows.
Here is the 30-60-90 plan I recommend and implement.
30 days: stand up the registry and cut silent access
Start with light, fast, and visible.
Stand up an AI use registry tied to data classification. Owner, purpose, model or service, scopes, data classes, and logs location. Make entries mandatory for access. This creates transparency and accountability.
Discover and contain Shadow AI. Inventory unapproved apps, add-ons, and OAuth connections. Revoke or sandbox where needed.
Triage egress. Add interim DLP and network rules for obvious leaks to AI services. Monitor API exports from SaaS linked to AI.
Educate loudly. Send a one-pager on AI attacks and the new process. Open a hotline so staff can request tools through the registry.
60 days: identity and data controls that actually bite
Priorities in this order.
SaaS posture and OAuth control across Microsoft and Google. Inventory all authorized apps. Prune scopes. Require SSO. Monitor token use.
Data labeling and egress rules for model traffic. Mark what AI can’t touch. Enforce NO_AI at the gateway and in DLP.
AI gateway policies as a guardrail, not a crutch. Add input and output rules that strip secrets, neutralize commands, and block unknown exfil paths.
Managed browser and extension allowlists. Kill the long tail of sketchy AI extensions.
Prompt injection testing in CI for RAG and agents. Treat untrusted content as adversarial input and break builds that fail.
90 days: wins, misses, and receipts
Wins I expect to show:
Registry coverage above 80% of active AI tools with owners who can answer scope questions.
Measurable reduction in high-risk OAuth scopes and fewer unapproved apps.
Fewer copy and paste events to free AI endpoints after communications and controls land.
Misses you should own:
One or two teams will keep using a favorite AI helper that is not in the registry. Catch it. Coach them. Move on.
A connector will misbehave again. Your logs and revocation plan should turn a headline into a footnote.
Receipts to keep:
Before and after OAuth app inventories.
Change records for revoked scopes and new approvals.
Prompt and output logging samples that prove guardrails worked.
Industry reality check: healthcare is copying PHI into AI
If you need a visceral nudge, look at healthcare. Clinicians and back-office teams are pasting protected health information into AI scribes and RAG notes to save time. The intent is good. The risk is obvious. Vendor defaults change. Sharing features leak. Logs go missing. The compliance hit lands on you. We saw public examples in 2025 where supposedly private AI content surfaced in search. The fixes are the same across industries: registry, data classes, scopes control, and logs you can defend.
Agents need adult supervision
Autonomous workflows sound magical until they act like a user that never sleeps, holds broad entitlements, and does not explain itself. Experts warned all year that we are trying to govern digital workers with rules built for humans. Shared accounts, static creds, and over-provisioned access were everywhere. The answer is boring and effective: unique identities for every agent, least privilege, dynamic permissioning with approvals, and a visible kill switch. Test agents with canaries and red team prompts before they ever touch production.
What I want boards to hear
Shadow AI is what happens when identity, data, and speed collide. Your risk lies in the connectors, scopes, browser, and agents that you do not inventory. LLM security matters, but AI governance is the center of gravity. If you want AI without regret, demand a registry, insist on logs, and fund the first 90 days as if they were deciding your 2026 audit. They do.
Key Takeaway: No logs, no trust. No trust, no AI.
Call to Action
👉 Get a 30-60-90 Shadow AI action plan template. Contact us and we will send it with a short walkthrough tailored to your environment.
👉 Subscribe for more AI security and governance insights with the occasional rant.




Going to discuss this with my Security Lead for sure. We were just discussing an internal audit where we discovered many unauthorized browser based AI apps being used.
So much here! Your knowledge of the subject is amazing. I plan on rereading this several times.